
Zama’s acquisition of Kakarot marks more than an exit. It signals the next phase of privacy-first infrastructure. Fully Homomorphic Encryption (FHE) has long been considered the holy grail of privacy: it allows computation on encrypted data without ever decrypting it. Yet for FHE systems to work securely, they need proof that the encrypted inputs were correctly formed. A lightweight, verifiable evidence that users encrypted their data properly before it entered the network.
That’s precisely where Kakarot comes in.
Over the past three years, Kakarot has evolved from a hacker house project in Lisbon to one of the most advanced teams in client-side proof generation. What began as an open-source project to build an Ethereum Virtual Machine inside Cairo, “what if you could write the EVM in a provable language?”, has grown into an essential bridge between zero-knowledge proofs (ZKPs) and FHE.
When LongHash Ventures co-led Kakarot’s seed round in 2023, the team’s focus was clear: make Ethereum provable inside a ZK-native stack. The result was Cairo-EVM, the first full implementation of Ethereum’s state transition function written in Cairo, achieving 100% opcode compatibility. Kakarot became an independent proving client for Ethereum, a “ZK hedge” that improved resilience across the ecosystem as all other ZK teams were converging on the RISC-V standard.
But the team never stopped iterating. By 2024, Ethereum scaling was largely a solved problem, thanks to the efforts of teams like zkSync, Base, Arbitrum One, OP, Polygon zkEVM, and others. Kakarot identified the next bottleneck: privacy at the user level. Instead of fighting for the pie, they decided to make the pie bigger by focusing on scaling privacy, enabling users to generate ZK proofs directly on their own devices.
This shift gave birth to Cairo M, a zkVM optimized for consumer hardware. Built on StarkWare’s S-Two prover, Cairo M achieved up to 10× faster proving times than the original Cairo 1 VM on CPU benchmarks, a breakthrough for client-side proof generation. It drastically reduced memory consumption, the key barrier for mobile proving.
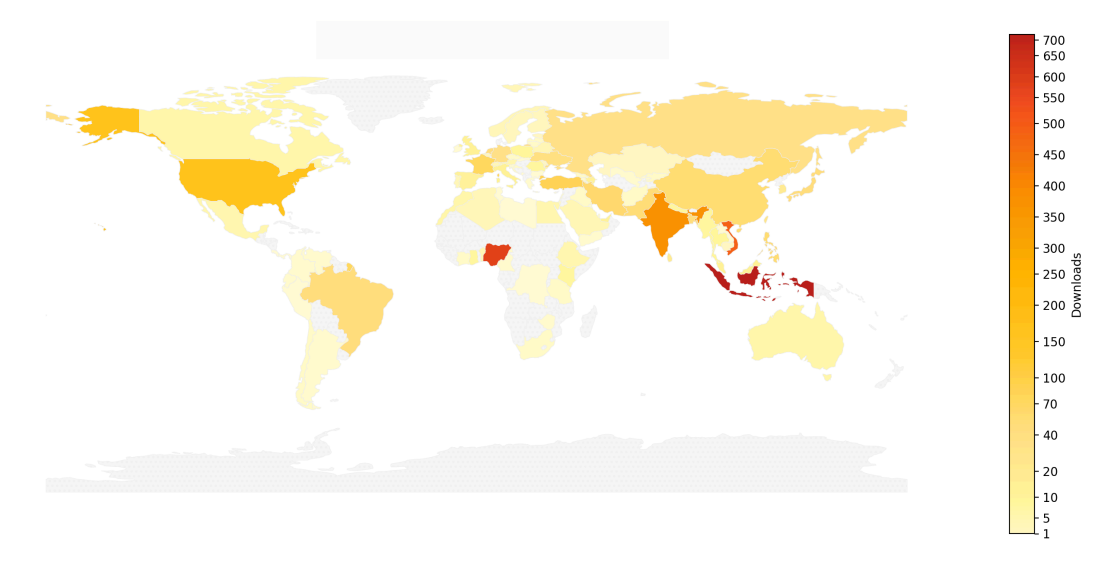
In October 2025, Kakarot and Hyli launched FibRace, a large-scale global experiment disguised as a mobile game. Over three weeks, more than 6,000 players across 99 countries generated 2.2 million proofs on 1,420 device models. The results were groundbreaking: most modern smartphones produced proofs in under 5 seconds, with a crash rate below 1%. FibRace proved that client-side proving wasn't just possible, it was practical, scalable, and ready for production.
Zama’s Confidential Blockchain Protocol uses FHE + MPC + ZK to bring confidential smart contracts to existing public blockchains. FHE handles encrypted computation, MPC decentralizes key management, and ZK verifies that the encrypted inputs are valid. The ZK component, crucially, must be lightweight and cheap to generate in a browser or mobile app, exactly the performance domain where Cairo M excels.
Why Kakarot fits perfectly into Zama’s stack:
Together, Zama and Kakarot are closing the loop. Zama ensures computation stays encrypted, and Kakarot ensures the encryption and computation can be verified efficiently on any device.
Zama envisions a world that evolves from HTTP → HTTPS → HTTPZ, where every interaction is end-to-end encrypted by default. Kakarot’s technology brings that vision to the edge, to the phones and browsers, where user data originates.
In this new model:
Client-side proof generation becomes the invisible equivalent of SSL certificates, a silent guarantee of integrity and confidentiality.
The acquisition validates three enduring lessons for builders and investors alike:
With Zama’s FHE and Kakarot’s Cairo M, privacy moves from promise to practice. The combination of on-device proofs and on-chain encrypted computation enables a new class of applications like confidential payments, private identity, secure AI, and beyond.
LongHash Ventures is proud to have co-led Kakarot’s seed round and to continue supporting founders who build at the intersection of deep cryptography and practical usability. The proof, as they say, is now in the phone and the future of the encrypted web is closer than ever.